Adversaries Targeting LATAM in 2025: Who They Are and How They Operate
Co-Written by Kate Esprit & Dmitry Bestuzhev
Executive Summary
Latin America experienced a 108% year-over-year increase in cyber attacks during Q1 2025. This amounts to an average of 2,640 weekly attacks per organization compared to 1,270 in 2024. This represents the highest regional growth across the globe.
The region’s unique threat environment encompasses financially-motivated cybercrime, nation-state espionage operations, and mobile malware campaigns targeting financial services.
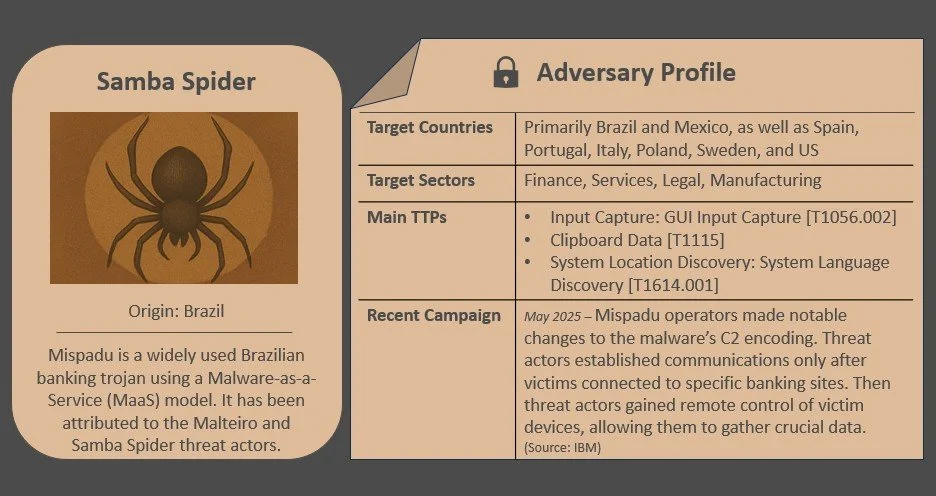
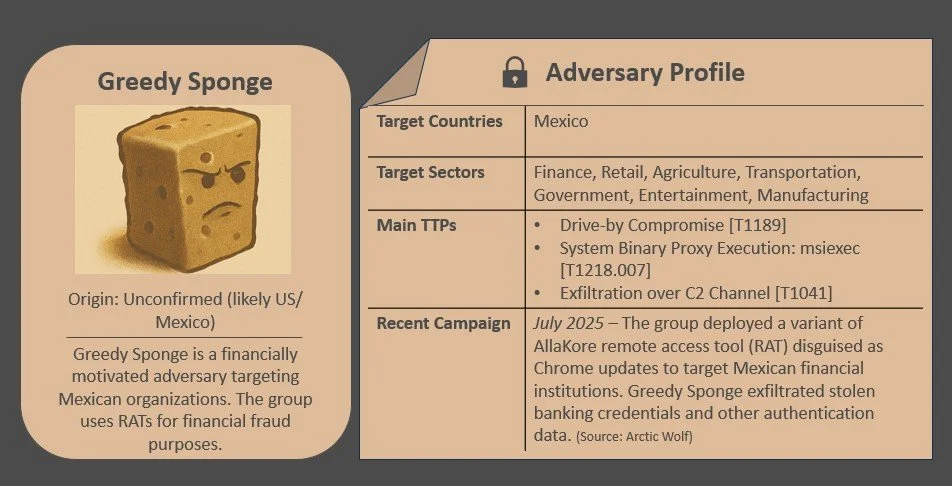
Regarding cybercriminal activity, the Golden Mexican Wolf ransomware group introduced physical penetration tactics against Mexican targets, SAMBA SPIDER continues to distribute modified versions of Mispadu malware across the region, and Greedy Sponge modified its toolset to bypass security controls in Mexico.
Chinese APT groups including Earth Alux, Earth Lamia, and FamousSparrow expanded operations across Brazil, Argentina, and Mexico, while Russian threat actors conducted espionage against Ecuadorian military communications.
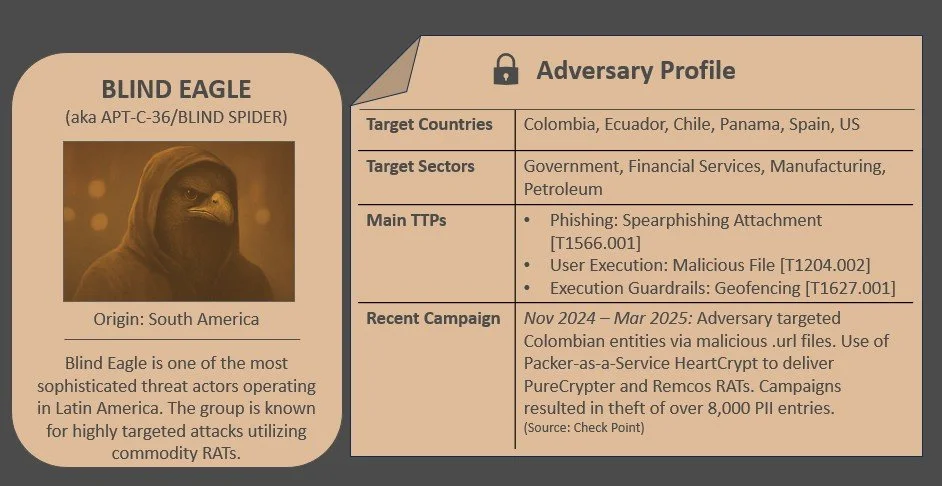
Blind Eagle leveraged new infection chains to deliver malware to victims in Argentina and Colombia, and researchers discovered new elements of Lebanese cyberespionage actors targeting the region.
Introduction
Latin America continues to face a rapidly evolving cyber threat landscape in 2025, driven by both financially motivated actors and state-sponsored adversaries. Ransomware remains one of the most pressing risks, with attacks surging across the region as threat groups exploit legacy infrastructure and unpatched systems. At the same time, banking trojans, Phishing-as-a-Service platforms, and commodity malware are fueling large-scale financial fraud campaigns that impact consumers and enterprises alike. Beyond cybercrime, state-aligned groups from Russia, China, and the Middle East are expanding espionage operations in Latin America, targeting critical sectors and government entities for strategic advantage. This report examines the latest trends shaping the region’s threat environment and highlights key adversaries that organizations should monitor to strengthen resilience.
Cybercrime/Financially Motivated Attacks
Ransomware Activity
Last year, the volume of ransomware attacks targeting the region increased by 259%. This year, the threat of ransomware persists in the region, often exploiting vulnerabilities in legacy infrastructure and unpatched devices. Victims in Latin America have been targeted by prolific groups such as Cl0p, whose global campaigns recently impacted Mexico. In April 2025, the Storm-2460 ransomware group exploited a zero-day vulnerability in Windows Common Log File System (CLFS) to extort money from victims in several countries, including Venezuela.
New ransomware actors have emerged in the region as well. In January, SCILabs discovered the Golden Mexican Wolf group targeting Mexico. The group's operations combined physical penetration of victim on-prem devices with digital ransomware deployment.
Mispadu Banking Trojan Operations
Latin America is home to many strains of banking trojans, which target online banking applications and frequently exploit Android mobile platforms. SAMBA SPIDER, which likely overlaps with Malteiro, is the threat group that operates the Brazilian Mispadu/URSA trojan and sells it to other adversaries based on a MaaS model. First publicly disclosed in 2019, Mispadu is written in Delphi and first targeted victims in Brazil and Mexico via spam and malvertising. However, SAMBA SPIDER has since expanded Mispadu’s operations across Latin America and Europe, previously harvesting more than 90,000 bank account credentials from 17,500 websites in 2023. Operators frequently use Mispadu to execute keylogging, browser overlay attacks, and socket-based remote control in order to steal financial data.
Greedy Sponge Targets Mexican Financial Institutions
In July 2025, Arctic Wolf updated its analysis of the financially-motived adversary Greedy Sponge. Active since at least 2021, Greedy Sponge is known for using customized variants of the open-source AllaKore RAT and its SpongeBob-themed memes on its C2. Greedy Sponge has also leveraged SystemBC, a C-based RAT used in the widely-publicized Colonial Pipeline ransomware intrusion in 2021. The group primarily targets Mexican corporations and financial institutions, particularly those with revenues exceeding USD 100 million. Greedy Sponge is known to gain initial access via spear-phishing and drive-by compromise, delivering AllaKore RAT to bypass two-factor authentication, and exfiltrating financial data from financial systems.
Chinese Cybercriminals Use Lucid for Smishing Attacks
Financially motivated groups were observed launching global attacks that impacted a significant portion of Latin America. In March 2025, Catalyst reported on the large-scale smishing attacks launched via Lucid, the new Phishing-as-a-Service (PHaaS) platform. This platform is run by Chinese cybercriminal group XinXin (a.k.a. Black Technology). Lucid provides phishing tools to subscribers registered in dedicated Telegram channels. Cybercriminal groups used Lucid to bypass SMS spam filters and steal credit card data from victims in Argentina, Brazil, Chile, Colombia, and El Salvador - among others.
State-Aligned APT Operations
Russia
In May 2025, Russian threat actor APT 28 (a.k.a. Fancy Bear) launched Operation RoundPress, a global espionage campaign utilizing spearphishing for initial access and exploiting cross-site scripting (XSS) vulnerabilities in web servers. Ecuadorian military entities were affected, with attackers gaining access to email data and establishing persistent email interception capabilities.
China
According to Diálogo Americas, the People's Republic of China (PRC) is the largest sponsor of cyberattacks in LATAM. Chinese state-sponsored activity, which has historically focused on Southeast Asian nations and the US, has expanded to target Latin America. PRC state-sponsored attacks are stealthy, leveraging custom backdoors, long-standing persistence, and strategic data exfiltration.
Chinese state-sponsored groups targeted Latin America through various operations in 2025:
Earth Alux conducted espionage operations by deploying custom backdoors such as VARGEIT throughout Asia and Latin America
Earth Lamia exploited web application vulnerabilities to target several industries in Brazil, India, and Southeast Asia
FamousSparrow (a.k.a. Earth Estries) deployed new variants of the custom malware SparrowDoor in Mexico, Honduras, and the US
Lebanon
In March 2025, the Lebanese APT Dark Caracal was identified as conducting espionage attacks targeting Latin American corporations. The group deployed Poco RAT malware for file upload, command execution, and system process tampering. Researchers discovered that Poco RAT shared similar characteristics with Bandook spyware, another custom tool leveraged by Dark Caracal. This most recent campaign is believed linked to ongoing targeting of Spanish-speaking users since 2022.
South America
Blind Eagle (a.k.a. APT-C-36) is one of the most sophisticated known threat actors operating in Latin America. The group is believed to be based in South America given its use of regional Spanish dialects and intimate knowledge of local institutions. Blind Eagle tends to target victims in South America, especially Colombia, Panama, Ecuador, and Chile, as well as Australia, Europe, and US. Last year, the group’s campaigns affected at least 1,600 victims and collected more than 8,000 PII entries. Blind Eagle’s campaigns utilize spearphishing for initial access, deployment of encrypted payloads, and use of commodity RATs such as AsyncRAT and Warzone RAT. Recently, this threat actor has also utilized legitimate, signed applications for DLL sideloading, crypters to encrypt code for detection evasion, and payload distribution via Bitbucket and GitHub.
Business Impact for LATAM Organizations
The threat landscape in Latin America continues to evolve rapidly, with both financially motivated and nation-state actors viewing the region as a high-value target. The documented increase in attack complexity, combined with the region's digital transformation, creates a complex security environment requiring sustained investment in both technical controls and regional cooperation mechanisms. Attack impacts now cascade beyond individual organizations, with single infrastructure breaches affecting hundreds of companies across multiple countries simultaneously, particularly targeting financial institutions and public administration which account for over 50% of regional incidents.
Successful attacks on major Latin American targets now typically involve MFA bypass, real-time transaction manipulation, and potential compliance violations across multiple jurisdictions - with attack dwell times extending months for threat actors. Organizations with stronger cybersecurity postures are gaining market advantages as weaker competitors face operational disruptions, regulatory penalties, and customer trust erosion from successful attacks.
Stay tuned for Part 2 of our series, which will be a deep dive into the Latin American malware ecosystem!
Kate Esprit is a Cyber Threat Intelligence Analyst and the Founder of Phishing for Answers
Dmitry Bestuzhev is a Cyber Threat Intelligence Researcher.