Conti: An Inside Look at Russia’s Powerful Ransomware Gang
Co-Written by Kate Esprit & Evan Gordenker
This post is a part of our ongoing Russia-Ukraine Conflict Series, a series of posts about the less reported aspects of the conflict and its implications for modern cyber warfare. If you are interested in making a donation to help victims in Ukraine, please consider this list of organizations.
Introduction
As outlined in last week’s post, the Russian invasion of Ukraine has prompted the involvement of underground hacking groups. While largely financially-motivated in nature, some of these cybercriminals have abandoned their usual “selling to the highest bidder” approach and are actively directing their hacking operations to support Russia or Ukraine. One of these groups, Conti, declared their support for Russia, vowing to retaliate against enemies of the Kremlin.
Meet Conti, a Russia-based ransomware-as-a-service (RaaS) gang believed to have been operating since at least 2020. Conti quickly established itself as one of the most sophisticated and ruthless ransomware hacking groups, having been linked to more than 400 cyberattacks. The group is known for stealing victims’ credentials to exploit remote network services or software vulnerabilities, then shutting down entire networks and demanding ransoms as high as $25 million.
Conti is particularly untrustworthy among ransomware gangs, as the group has previously refused to return victims’ data even after a ransom is paid. The group has also utilized double extortion, in which a victim is told to pay a ransom in exchange for the release of their encrypted data while simultaneously being threatened with the public release of this data if the ransom is not paid. In May 2021, Conti targeted Ireland’s public healthcare service, HSE, in a cyberattack which crippled the country’s medical infrastructure. The hackers gave HSE a decryptor to restore the lost data, with the understanding that Conti would still leak the stolen information if HSE refused to pay the $20 million ransom.
Russian Support and Ukrainian Clapback
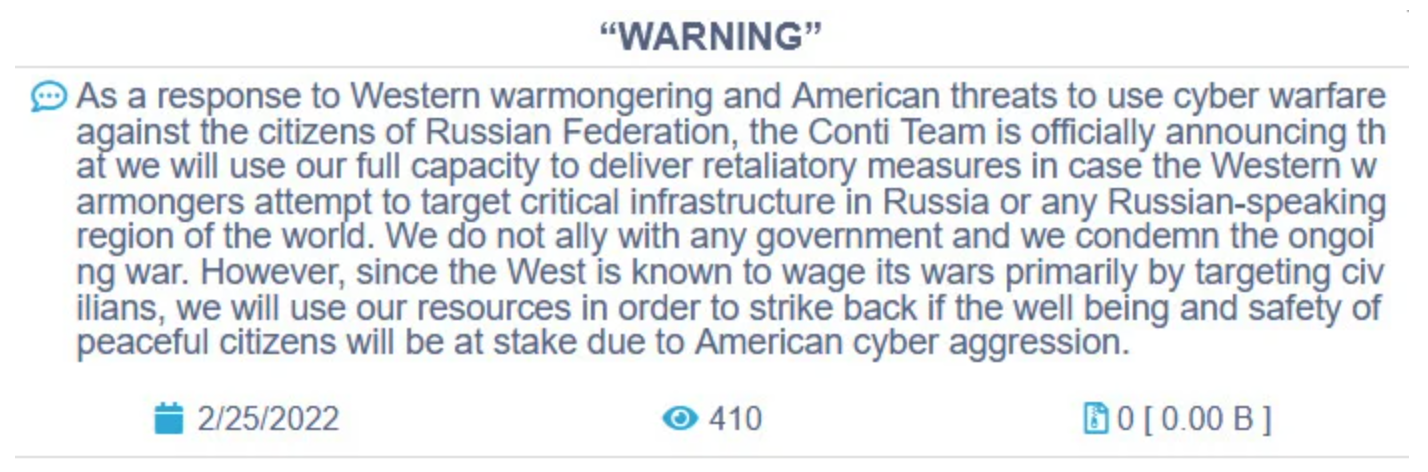
On February 25, 2022, Conti released the below statements to state the group’s full support of Russia and threatening any enemies of the Kremlin.
Official Conti announcements proclaiming support for Russia in the invasion (Source: Conti Leaks Blog)
However, Conti’s bold announcements in favor of Russia may have not had the intended effect. Just two days after the group allied itself with the Kremlin, the Twitter user @ContiLeaks did to Conti what the hacking group had done to many of its victims - leaked sensitive data. ContiLeaks is believed to be an unidentified Ukrainian security researcher. Specifically, the user publicized troves of Conti’s internal data, including the group’s source code and internal communications.
The leaked information included more than a year’s worth of Conti’s private messages, posted via messaging services Jabber and Rocket.Chat. According to these chat logs, Conti appears to have been linked directly to Russian intelligence services. Specifically, Conti was observed receiving orders from the Russian Federal Security Service (FSB) to hack a contributor of Bellingcat, an investigative journalism group working on a story concerning jailed Russian dissident Alexei Navalny. The link between Conti and the FSB is detailed in a series of tweets by Christo Grozev, the executive director of Bellingcat.
In the initial aftermath of the leaks, Conti was reportedly still conducting its usual hacking operations, as evident by the group’s publication of new victims on its site. However, as the cybersecurity community has been taking full advantage of the new publicized data containing intimate details of Conti’s organization, infrastructure, and tools, it seems that the group has gone off the grid. According to a report by Cyberint, Conti’s senior leaders initially shut down the gang’s infrastructure, deleted files, and discontinued communications. Recent intelligence reports suggest the gang has since resumed operations.
Historic Targeting of Conti
Conti is no stranger to having to readjust its direction after being publicly targeted. Here are a few examples of previous law enforcement operations that have affected the group:
FSB officers executing arrests of REvil members
(Source: Bloomberg Quicktake: Now)
January 2022: Russian authorities arrested members of Conti’s main competitor, REvil, at the request of the US government. Prior to these arrests, Russian officials were also carrying out an investigation into Conti, though the group was never affected by the arrests and one member of the gang confidently announced they had been assured that Conti would not be affected by law enforcement.
Some international affairs experts characterized the REvil arrests as an effort to placate the US government while Russia prepared for the invasion of Ukraine.
January 2021: A collaborative law enforcement effort against Emotet, a sizable botnet, resulted in the seizure of servers used to control Emotet and the arrest of some of its operators.
At the time, these actions spooked Conti and the group rearranged under new aliases.
September 2020: The US National Security Agency (NSA) and Cyber Command launched an operation to cripple the TrickBot botnet, which was the largest operational botnet at the time. That botnet was a critical source of compromised systems.
The operation set a precedent for governments to strike back at cybercrime groups.
At the End of the Day, It’s a Business
As stated previously, Conti has a reputation for being a particularly ruthless and greedy ransomware operator. Although this band of hackers is known for its sophisticated and innovative ransomware campaigns, the recent leakage of their chat logs shows that Conti deals with its share of office dramas like any organization.
The chat logs shown below are snapshots of Conti members’ conversations via Jabber and expose the inner workings of a ransomware gang. Managers complain of poor performers, staffers complain of being denied vacation days, and many appear to be dissatisfied with their pay.
Operator “Specter” characterizes Conti engineers as lazy (Source: Conti Leaks Blog)
Operator “Mango” appears to complain of pay (Source: Conti Leaks Blog)
Conclusion: Business is Booming
Despite the group’s relative lack of online engagement this past week, Conti is not going anywhere. Per the US Cybersecurity and Infrastructure Security Agency’s (CISA) updated alert issued March 9, 2022, Conti’s ransomware operations have surpassed 1,000 total attacks.
Conti conducts business through cryptocurrencies and relies heavily on Bitcoin. According to blockchain data platform Chainanalysis, the group received at least $180 million in ransom payments in 2021. Some report that the group has over $2 billion worth of Bitcoin. Such profitability likely indicates ransomware will continue to be a lucrative source for cybercriminals around the world. The growing cost of ransomware attacks has also affected cyber insurance premiums, which dramatically increased by 34% in Q4 of 2021.
Based on what the cybersecurity community knows about Conti, the gang appears amenable to assisting in Russian government operations. This will reduce the likelihood that Conti or other Russian cybercrime groups are brought to justice. Given the current escalation of tensions between Russia and the rest of the world, the chances of a REvil-like wave of arrests appears to be slim. Even less likely is the actual cessation of criminal ransomware operations, so it is safe to assume for the time being that Conti will continue to target victims around the world.
Evan Gordenker is a Senior DFIR Consultant at Unit 42. He specializes in combating user data scraping and providing intelligence-driven threat mitigation.
Kate Esprit is a Cyber Threat Intelligence Analyst at MITRE and the Founder of Phishing for Answers.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 22-0870. The author's affiliation with The MITRE Corporation is provided for identification purposes only, and is not intended to convey or imply MITRE's concurrence with, or support for, the positions, opinions, or viewpoints expressed by the author.'©2022 The MITRE Corporation. ALL RIGHTS RESERVED.