Hacker Spotlight: Guacamaya
Phishing for Answers’ “Hacker Spotlight” is a series of posts analyzing different cybercriminal groups in Latin America. Each post will focus on a different adversary and provide details on each group’s operations, signature techniques, victimology, evolution, and recent campaigns. The objective of this series is to bring awareness to the cyber threat landscape in Latin America.
Overview
Source: Forbidden Stories
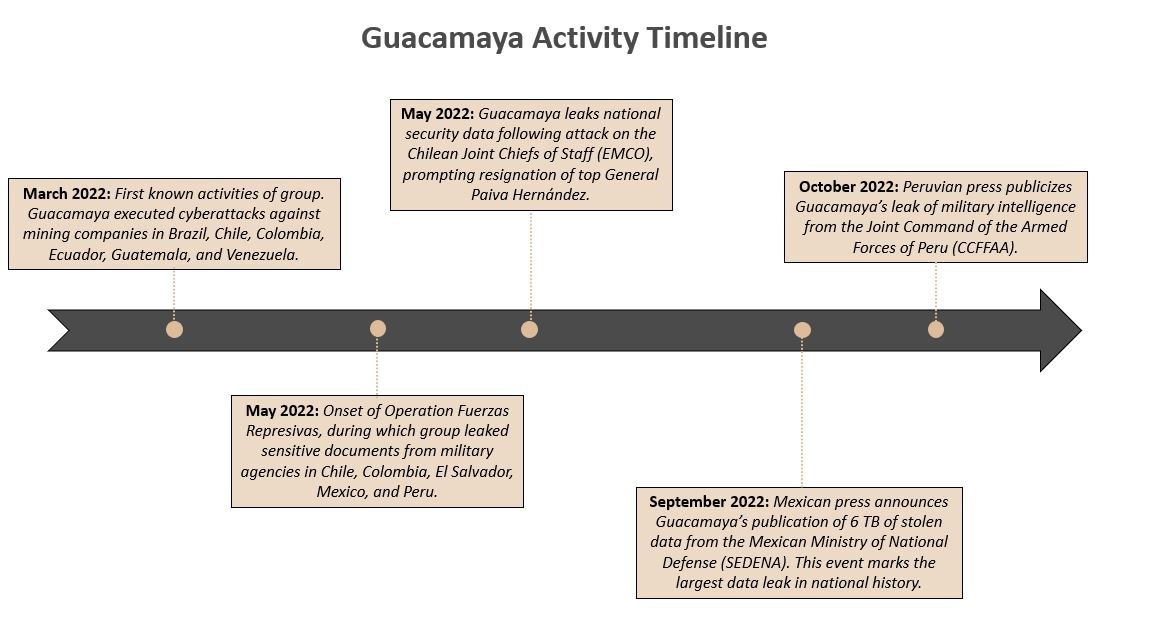
Guacamaya, the Mayan word for macaw, is a hacktivist group operating in Latin America. The group targets government organizations, military agencies, and extractive industries such as mining. Guacamaya’s mission is to support “all people affected by the invasion and dispossession of Abya Yala [named used by indigenous communities to describe the Americas].” Between June and October 2022, Guacamaya launched Operation Fuerzas Represivas , a series of large-scale leaks that released data stolen from government and military agencies in Chile, Colombia, El Salvador, Mexico, and Peru. This threat actor’s campaigns often leverage software vulnerabilities, Python scripting, and living off the land (LOTL) techniques during their attacks.
Background Information
Evolution
The graphic below shows the evolution of Guacamaya’s operations beginning from the group’s first reported activities until present day. This analysis, which is based on open-source data, shows how this adversary’s operations have impacted countries across Latin America in a relatively short period of time.
Recent Campaign
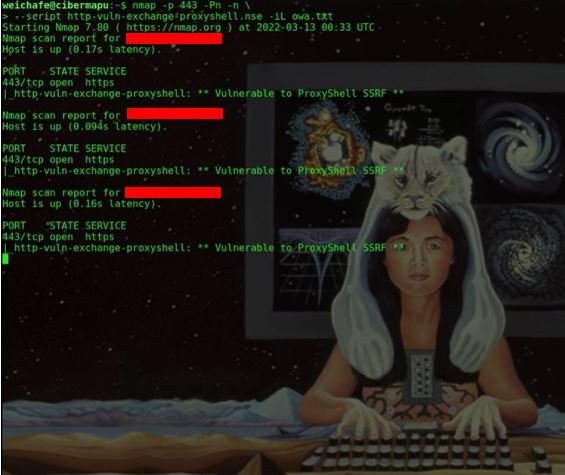
Guacamaya’s code used to exploit ProxyShell vulnerabilities to target SEDENA. (Source: Enlace Hacktivista)
FUN FACT: Following their attack against SEDENA in Mexico, Guacamaya released a video showing all of their code and procedures during the attack. The full video can be found here.
In September 2022, Guacamaya released 6 TB of data stolen from the Mexican Ministry of National Defense (SEDENA). The leak, which represents the largest data leak in Mexico’s history, contained a trove of communication records dating back to 2010. The stolen data revealed controversial actions taken by various Mexican army officials and politicians, including the government’s use of spyware against citizens, the military’s concealment of sexual abuse cases, and updates surrounding the military’s role in the Ayotzinapa case. News reports indicate that it could take years for all of the hacked information to be verified and publicly confirmed.
During a recent interview with Recorded Future, Guacamaya expressed sentiment that the public was beginning to understand its mission. When asked if the group was planning further data leaks, Guacamaya’s members responded: “This question could be asked of the large extractive companies and their political entities[…] In that sense, as we mentioned before, our task will be to use this tool, as another one for the joyful rebellion, the just resistance.” Only time will tell if the group will continue its operations…
Resources for Further Reading:
Forbidden Stories: https://forbiddenstories.org/the-struggle-of-one-territory-must-be-the-struggle-of-all/
Enlace Hackivista: https://enlacehacktivista.org/index.php?title=Fuerzas_Represivas
Cyberscoop: https://cyberscoop.com/guacamaya-hacktivist-group-latin-america-interview/
The Record: https://therecord.media/mexican-president-confirms-guacamaya-hack-targeting-regional-militaries
Approved for Public Release; Distribution Unlimited 23-02410-3. ©2023 The MITRE Corporation. ALL RIGHTS RESERVED.