How I Got My First Job in Cybersecurity
Introduction
It is no secret that the number of vacant cybersecurity positions outweighs the number of professionals to fill these roles. According to a recent press release issued by Cybersecurity Ventures, the number of unfilled cybersecurity jobs is projected to reach 3.5 million by 2025. Cybersecurity is a highly specific and technical field, but contrary to what people might think, employers are not solely seeking engineers and programmers. The industry is growing to include any professional willing to work hard enough to be a part of the conversation. And I was fortunate enough to become one of those professionals.
As a person who always preferred English to math, Spanish to science, and books to computers, transitioning into cybersecurity was not easy for me. For 5 years, I had pursued a career in business intelligence and compliance risk. However, I began to realize how unhappy and unfulfilled I felt, and became determined to start my journey to cybersecurity. After 2 years of learning about information security, studying for certifications, and networking with industry leaders, I found my first job in the field! Here are some details about how I landed that first opportunity, as well as some tips for starting your own cyber journey.
1. Make a list of your interests and passions, and let that serve as career guidance.
This field encompasses countless career paths, from software development to penetration testing to digital forensics. Therefore, it is crucial to make a list of things that drive you professionally. Make sure to include the interests that are most important to you, and which other interests are less important. These can be considered as career “negotiables” and “non-negotiables.”
Non-negotiables: These are the things about which you are most passionate. These are aspects of your career that you are less willing to compromise on - they make you who you are.
Negotiables: These are things that you enjoy, but are less important than the non-negotiables. These can be considered “secondary interests,” or aspects of your career you would like to have but can ultimately do without if needed.
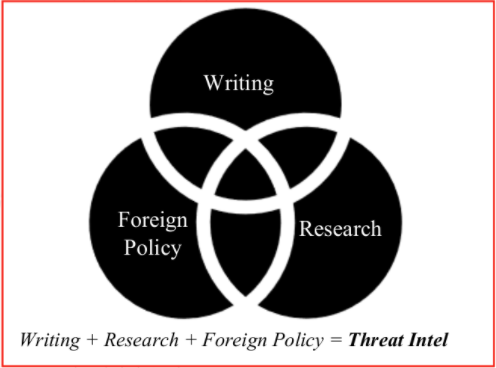
As an example, one of my own negotiables was speaking foreign languages. This was something that I absolutely love to do, but I would be willing to accept a job that did not utilize this skill. My non-negotiables included intelligence research, writing about criminal behavior, and analyzing foreign policy. These aspects form the core of my passions and thus, it was important to me to ingrain these interests into my future role. As shown in the diagram, the field of cyber threat intelligence comprises all of my non-negotiables and that was when I decided to pursue threat intel positions.
2. Talk to industry professionals of varying experience levels.
During your cyber journey, you are undoubtedly going to be speaking with professionals who are already in the industry. However, many people tend to target those with executive titles and 10+ years of experience. While you can certainly learn from conversations with CISOs and industry leaders, consider also speaking with people who recently joined the industry. Depending on their level of experience, every person will have something different to bring to the conversation.
Here is a good range of industry professionals to target:
The veterans - people who you want to become in 15-20 years
The experienced - people you want to become in 5-10 years
The newbies - people you want to become in 2-5 years
The brand newbies - people who are also starting their cyber journey
3. Network with purpose.
Inevitably, networking is going to be part of your cyber journey. Remember that networking should always be more than just a conversation. To get the most out of networking, it is most helpful to plan ahead. Think about what has compelled you to have a conversation with this particular individual and the questions you are most curious to ask them. Additionally, remember that networking should always be a two-way street - meaning it is not always about what another person can do for you. Consider some ways in which you could be helpful to somebody else. One thing that I did for a particular mentor was to re-share all of their content on LinkedIn. Whenever my mentor announced a new publication, speaking engagement or other career-related update, I promoted it within my own LinkedIn network to increase visibility. This might not seem like much, but it was my small way of giving back.
Of course, speaking with recruiters is much different than speaking with other people in your network. Here are 5 tips for successfully interacting with a recruiter:
Remember to ask them about their career journeys. This first step is crucial, because many people become consumed with asking recruiters about job opportunities and forget how to navigate the interaction. It is a great practice to ask recruiters about their own experiences and interests. As a bonus, demonstrating interest in another person’s journey will likely help you stand out from other candidates.
Be able to deliver your “elevator pitch” in no more than 30-45 seconds. People tend to become less engaged in a conversation after 1 minute. Prepare beforehand how you want to summarize your experience, passions, and future goals. Practice in front of the mirror, so that when the time comes, you can clearly and concisely articulate yourself in front of the recruiter.
Share something memorable about yourself. It can be daunting to think about what makes you unique. However, the task may be much easier if you made your list of negotiables and non-negotiables. It is highly likely that your non-negotiables will directly indicate what makes you special. For instance, one of my non-negotiables was writing because I have always loved it. Because of this passion, I launched a blog (this one, in fact!) in which I hope to build a community of readers who share my love for cybersecurity. I frequently discussed my blog during conversations with recruiters because it is memorable and it is an important part of my professional goals.
Make eye contact. This one speaks for itself, but it goes a long way.
Follow up after the initial conversation. Recruiters interact with many people every day and even if you have made an excellent impression, it is important to keep in touch with them. After the initial meeting, send the recruiter an email thanking them for their time and add some reminders about what was discussed.
4. Be a tireless learner.
Cybersecurity is an ever-evolving field that demands lifelong learning. It is virtually impossible to become an expert in all aspects of cybersecurity, as hackers will always find new methods of exploiting networks. Therefore, it is important to find ways in which you can continuously learn about the industry.
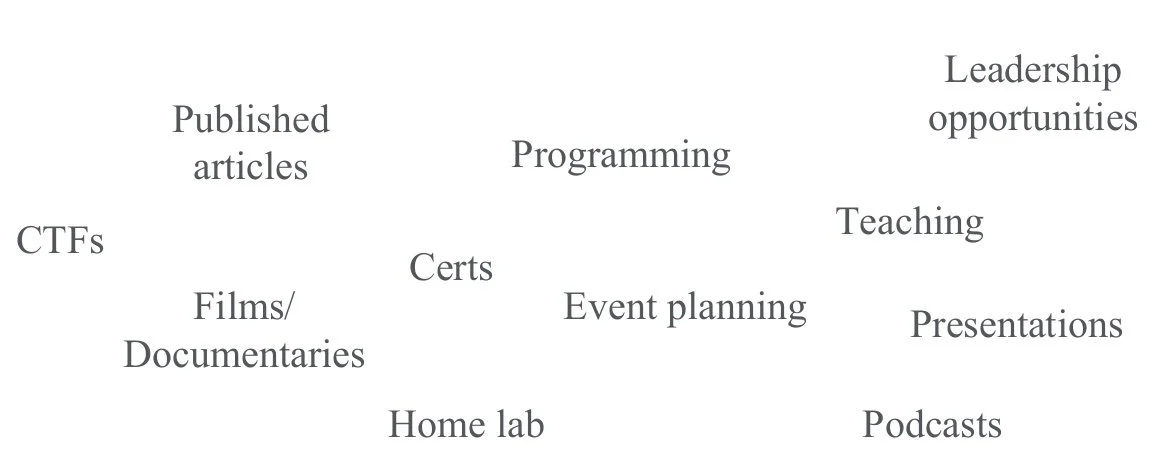
In order to be a learner for life, there is one major rule: Make it fun. Identify a way of learning that you enjoy, rather than something that feels mandatory. Maybe you are a professional who loves listening to podcasts - that can be a very effective way to keep abreast of industry developments. Or possibly you have an affinity for capture the flag (CTF) competitions, which can be a great way of addressing security-related challenges. As stated previously, I love to write so I have found my learning medium through this blog as well as writing research articles for industry publications.
5. You can have doubts, but don’t give up!
This is perhaps the most crucial step of all. Imposter syndrome can affect anybody, especially those of us who are new to cybersecurity. Personally, sometimes I still have difficulty with knowing I’m in a STEM-based field despite having struggled in math and science classes all my life. I have many more technical skills to learn and refine compared to other people in the field, and that is okay. Having moments of self-doubt and setback is natural, as long as you stay dedicated to pursuing your goals.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 22-0256. The author’s affiliation with The MITRE Corporation is provided for identification purposes only, and is not intended to convey or imply MITRE's concurrence with, or support for, the positions, opinions, or viewpoints expressed by the author. ©2022 The MITRE Corporation. ALL RIGHTS RESERVED.