How to Stay Cybersafe During the Holidays
‘Tis the season…to make cybersecure decisions!
And just like that, the year of 2021 is almost at a close! The holiday season is now fully upon us, and while this time of the year brings us joy, gifts, and extended visits with family, it also means an exponential increase in online shopping, insecure web browsing, and unmonitored enterprise networks. It is important to remember that just because most people are on vacation and taking a break from work during this time does not meant that cybercriminals are also relaxing.
Indeed, cyber threat actors often see the holidays as the best time to execute attacks. Recently, the US Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) issued a warning about the increase in ransomware attacks occurring during holidays and weekends. Additionally, a survey conducted by the cybersecurity company Cybereason found that 89% of respondents, all of whom had previously been victims of cyberattacks during the holidays or weekends, reported concerns over the potential for a repeated attack during the 2021 holiday season.
With reduced monitoring of IT systems and networks, an overwhelming increase in traffic to consumer websites, and the ongoing supply chain shortages, the holidays can create an opportunity for cyber exploits. However, with some simple steps, you can ensure that your holiday season is joyful and your online information and businesses are protected.
Methods to remain cybersafe during the holidays
For the Consumer:
Do not click on suspicious links in emails, messaging platforms, or social media sites. Phishing attacks and online scams are becoming more sophisticated, but it is crucial to stay vigilant and recognize messages from unknown senders.
Upgrade software and operating systems to the most current versions, including antivirus and anti-malware scanning systems.
Utilize strong passwords and frequently change them. Avoid reusing passwords across multiple accounts and store all log-in credentials in a secure location.
Ensure multi-factor authentication (MFA) for all online services when possible.
Practice secure web browsing through the use of secure shell (SSH) or secure sockets layer/transport layer security (SSL/TLS) encryption.
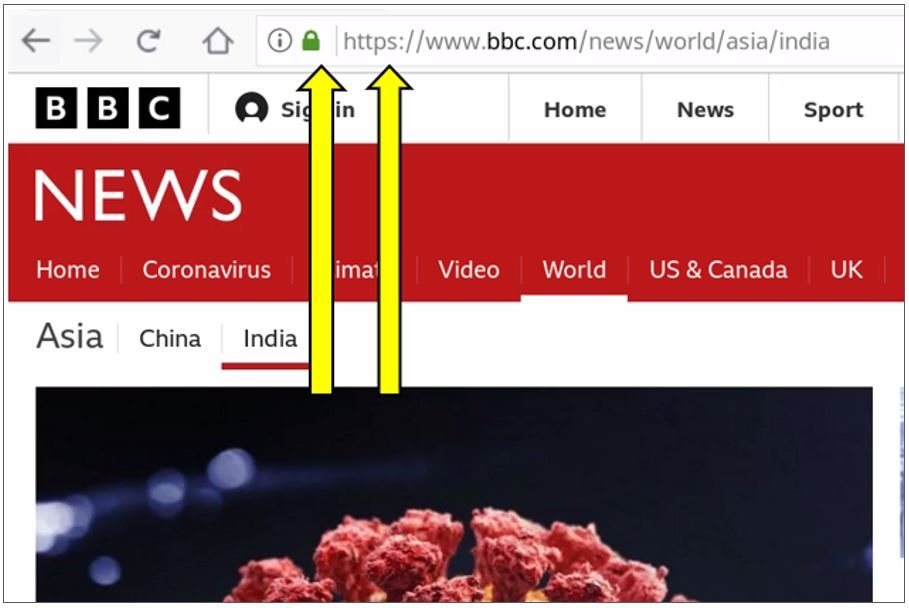
Tip #1: If the website URL you are browsing begins with an https://, then you are using encryption! If the URL beings with an http://, then you are transmitting data in plaintext that can be intercepted by a malicious actor.
Tip #2: If your web browser shows a lock icon to the left of the URL, then you are browsing securely! If there is no lock shown or the browser window reads “Not Secure,” then you are not browsing with encryption.
For the Business:
Conduct awareness trainings for all staff. While this step is not new to information security managers, regular trainings on the severity of phishing, social engineering, and other cyber threats can make a difference. It is also critical to emphasize how employees should report unusual or suspicious messages to internal IT teams.
Maintain an offline, encrypted backup of company data and regularly test these backups. If possible, follow the “3,2,1 Rule,” which necessitates having 3 sets of data on 2 different media types, with at least 1 of the backups being stored offsite.
Implement network segmentation to avoid a single point of failure. The use of segmentation strategies such as demilitarized zones (DMZs) and virtual local area networks (VLANs) can help businesses avoid concentrating all the data in a single central hub within the network.
Take steps to harden networks and devices against malicious intrusion attempts. Network hardening techniques can include the following:
Changing default credentials
Upgrading firmware
File hashing
Disabling all unused ports and unnecessary services
Utilizing secure protocols
Have incident response and contingency plans in place in the event of an incident. These plans should include procedures of how to notify and respond to an intrusion, as well as how to circumvent the inaccessibility of affected systems in order to ensure some continued business operations. Most importantly, socialize these plans across all departments.
Conclusion
While it is critical to prioritize security hygiene throughout the year, this particular period can be especially vulnerable for consumers and business organizations. Maintaining vigilance and adhering to the above-cited best practices can help to ensure that your holidays are full of peace, happiness, and of course, cybersecurity. Whatever your plans are for this month, Phishing for Answers wishes you a joyful and safe holiday season!