#howitworks: Internet of Things (IoT)
The #howitworks series aims to help readers to gain a basic understanding of important technologies and related security implications. This series is a part of Cybersecurity Awareness Month, which is dedicated to raising awareness about cybersecurity issues and data protection.
Starting with Alexa
“Alexa, play Lady Gaga at volume six.”
“Alexa, add fruit, bread, and peanut butter to my shopping list.”
“Alexa, show me pictures of kittens.”
These are just a few commands that can be given to the Amazon Alexa, a cloud-based voice-enabled service. Alexa, as well as Google’s Assistant and Apple’s Siri, represents a significant milestone in the virtualized world. These services allow consumers to manage their schedules, check active timers, and control music playback – all through the simple use of the human voice. But how exactly does Alexa listen, process signals, and respond without being…human? The answer is through the application wireless communications, natural language processing, and the Internet of Things (IoT).
Introduction to IoT
The Internet of Things encompasses physical devices that are connected to the Internet and are able to share data with other devices. Specifically, IoT devices maintain Internet connections via sensors, software, and data processing and analysis. IoT technologies have the ability to transfer data to other “things” without any human interaction. In addition to Alexa, common examples of IoT devices include: the Apple Watch, heart rate monitoring systems, fitness trackers, robot vacuum cleaners, and the Peloton bike. So-called “smart” technology, or self-monitoring analysis and reporting technology, leverages IoT to allow functionality for devices like iPhones and tablets.
How does IoT work?
IoT devices generally utilize Wi-Fi connections and sensors in order to communicate and share data. It helps to think of IoT as comprising many different mini computers which are connected to the Internet. These mini computers process data in 4 simple steps:
IoT devices use sensors to receive data from the surrounding environment.
Next, this data is sent by the sensors into the cloud via wireless connections (e.g. Wi-Fi, Bluetooth, satellite, etc.)
When the data arrives in the cloud, the device’s software processes and analyzes the information.
Finally, the processed data is transmitted to the user in a useful way (e.g. alert, notification, voice-activated response, etc.)
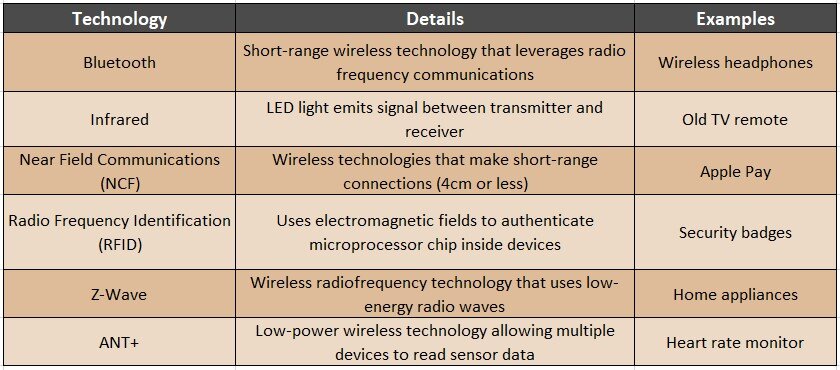
Additionally, the use of artificial intelligence (AI) by IoT technologies is becoming increasingly valuable, given that AI can help these devices process language (like voice-enabled commands) and retain information through machine learning algorithms. More explicit examples of IoT technologies and their functions are shown in the table below.
IoT Security Concerns
Just like anything connected to the Internet, IoT is vulnerable to various security threats. Here are some of the most significant security concerns associated with IoT devices:
User Privacy: As IoT devices become more sophisticated and adept to anticipating the needs of consumers, more user data is stored in these devices. Confidential user data, such as voice, biometric, and payment information, is increasingly given to IoT devices without users being aware of how much of their privacy is being sacrificed. Additionally, the scale of potential IoT breaches is enormous given the synchronous nature of IoT data transfer between other smart devices.
Insecure Data Storage: Unlike computers, IoT devices do not require any physical user intervention in order to operate. This lack of physical hardening can make IoT technologies vulnerable to external threats, especially if these devices are kept in remote locations for extended periods of time. Also, given that IoT stores data on remote servers over the cloud, there is an increased potential for this data to be compromised. This lack of security is amplified due to the fact that regularly patching and updating IoT device software can be challenging.
DDoS Attacks: The development of IoT technologies often uses similar hardware and software. This common underlying structure creates a pathway for malicious actors can gain access to a network. This unifying attack vector, in addition to a lack of regular software updates, makes IoT devices ideal targets for denial-of-service (DoS) attacks. IoT is particularly vulnerable to permanent denial-of-service (PDoS) attacks, which cause permanent damage to the devices. IoT is a relatively new technology, and therefore, much remains to be learned.
For more information regarding DoS attacks, see Phishing for Answers’ previous #howitworks post.
Want to learn more about a specific technology during Cybersecurity Awareness Month? Leave a comment down below with your suggestions!