#latamhackers Series: Week 2- Commodity Tools
This post is a part of our #latamhackers series, a 5-week series about some of the top techniques used by hackers in Central and South America.
#LatAmHackers Series - Brief Recap
During our 5-part series, Phishing for Answers will detail the most utilized hacking techniques in Latin America. Each post will include a summary of the technique, a recent example, and recommended mitigation measures.
Last week, we discussed how regional hackers utilize phishing to gain access to victim networks (read more here: #latamhackers Series: Week 1 - Phishing). This week is all about how these groups use publicly available tools to infect target systems.
Here is the full list of techniques:
1. Spearphishing
2. Commodity tools
3. Reliance on user execution
4. Geographical targeting
5. Overseas tool expansion
Week #2: Commodity tooling
Summary:
Advanced persistent threats (APTs) in other parts of the world are known for creating novel malware. By contrast, hackers in Latin America largely rely on commodity malware, remote access tools (RATs) and software. While some groups have certainly been known to build custom tools (e.g., Poseidon Group was known for creating new malware), most utilize variants of public malware projects. This is because many regional APTs lack sufficient resources and infrastructure to create their own tools.
Example:
BLIND EAGLE, also known as APT-C-36, is a sophisticated group of hackers believed to be based in Colombia or Venezuela. BLIND EAGLE frequently compromises victims via commodity RATs, which the group often modifies or tailors to fit a specific purpose.
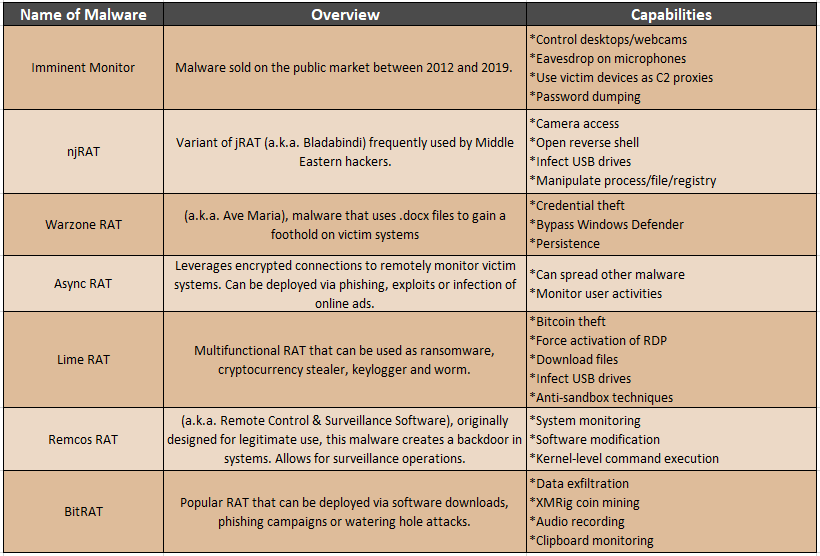
Below is a list of the known open-source malware that BLIND EAGLE has used against victims. Most of these are RATs that allow for capabilities such as keystroke logging (keylogging), remote control of devices, and infecting Windows operating systems.
(Publicly-available tools used by BLIND EAGLE, a hacker group likely based in Latin America)
Mitigation measures:
Open-source malware is beneficial for hacking because the source code is publicly available. Cyber teams responsible for endpoint detection and response (EDR) should habitually check code repositories and incorporate the signatures of known malware into detection technologies. As a general practice, all users should be able to recognize the warning signs of malicious software – slow browsing, the appearance of new programs or icons, pop-up messages, and continuous system crashing. Even adhering to basic cyber hygiene, such as regular updating of web browsers and downloading apps from trustworthy sources, can make a difference in protecting systems from malware.
Coming Up Next Week – Technique #3
Next week, the #LatAmHackers series continues with a discussion of the next technique – reliance on user execution. This post is all about the strategies used by Latin American cybercriminals to entice users to interact with malware and deploy it on a network.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 22-02304-2. ©2022 The MITRE Corporation. ALL RIGHTS RESERVED.