Russian Threats to Critical Infrastructure: The Past, Present and Future
This post is part of our ongoing Russia-Ukraine Conflict Series, a series of posts about the less reported aspects of the conflict and its implications for modern cyber warfare. If you are interested in making a donation to help victims in Ukraine, please consider this list of organizations.
The Present
On April 20, 2022, cybersecurity agencies in the US, Australia, Canada, New Zealand, and the UK released a joint alert about how the Russian invasion of Ukraine could pose a cybersecurity risk to organizations around the world. Specifically, there are many concerns of an increase in malicious activities orchestrated by Russian state-sponsored actors against critical infrastructure targets. According to a recent statement issued by US President Biden, the Russian government is believed to be constantly searching for new opportunities to exploit networks.
So what exactly is critical infrastructure and what makes it so critical? Critical infrastructure is defined as the infrastructure upon which societies depend to run effectively – basically, systems which are vital to our everyday lives. Think of assets like power generators, water dams, nuclear power plants, air traffic control systems, cellular towers, and satellites. If any of these technologies were to be compromised, societies and economies would be paralyzed.
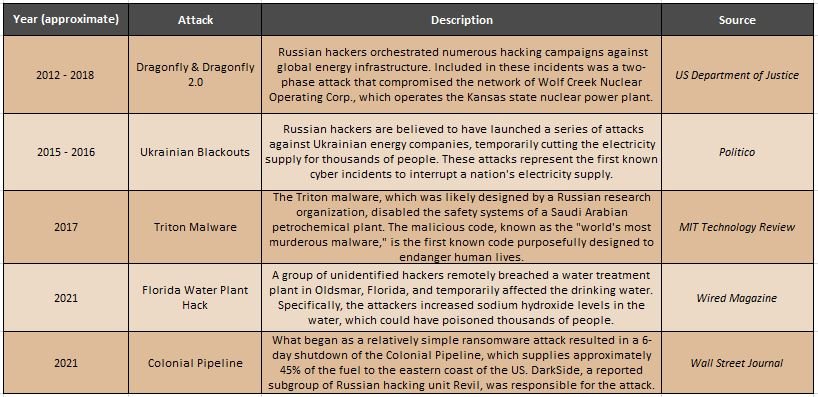
The truth is that cyber threats to critical infrastructure are not recent developments. Russian advanced persistent threat (APT) groups have been targeting critical networks around the world years before the invasion of Ukraine. Let’s take a look at historical examples of how critical infrastructure has been compromised.
The Past
Please note that this list is not exhaustive.
The Future
In an interconnected world, most of our critical infrastructure is either entirely network-based or mostly dependent on digital technologies. Even contingency plans hinge on the necessity of network connectivity. For instance, if the water in your home stops running, then the next logical response would be to contact your utilities provider. But what if cell towers are down and you can’t make phone calls from your cell phone? What if the power is out and you can’t submit an online service request? Unfortunately, these “what if” questions are not hypothetical anymore. As demonstrated earlier, the world has already experienced the collision between the cyber and physical worlds, all with real world consequences.
It is time for governments and civilians alike to start preparing for future instances of attacks on critical infrastructure. And when it comes to cyber kinetic threats, it is crucial to secure digital and physical assets. Implementing measures such as software patching, web application firewalls, and authentication timeout are useful in securing cyber infrastructure, but we cannot forget the offline strategies as well. Maintaining hard copies of important procedures, ensuring the availability of physically disconnected backups, and even storing manual or analog systems can all aid in mitigating critical infrastructure attacks.
By focusing on resilience as much as mitigation, the world can strengthen its technologies and begin to defeat hackers in this race towards cyber power.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 22-1326. The author's affiliation with The MITRE Corporation is provided for identification purposes only, and is not intended to convey or imply MITRE's concurrence with, or support for, the positions, opinions, or viewpoints expressed by the author.'©2022 The MITRE Corporation. ALL RIGHTS RESERVED.